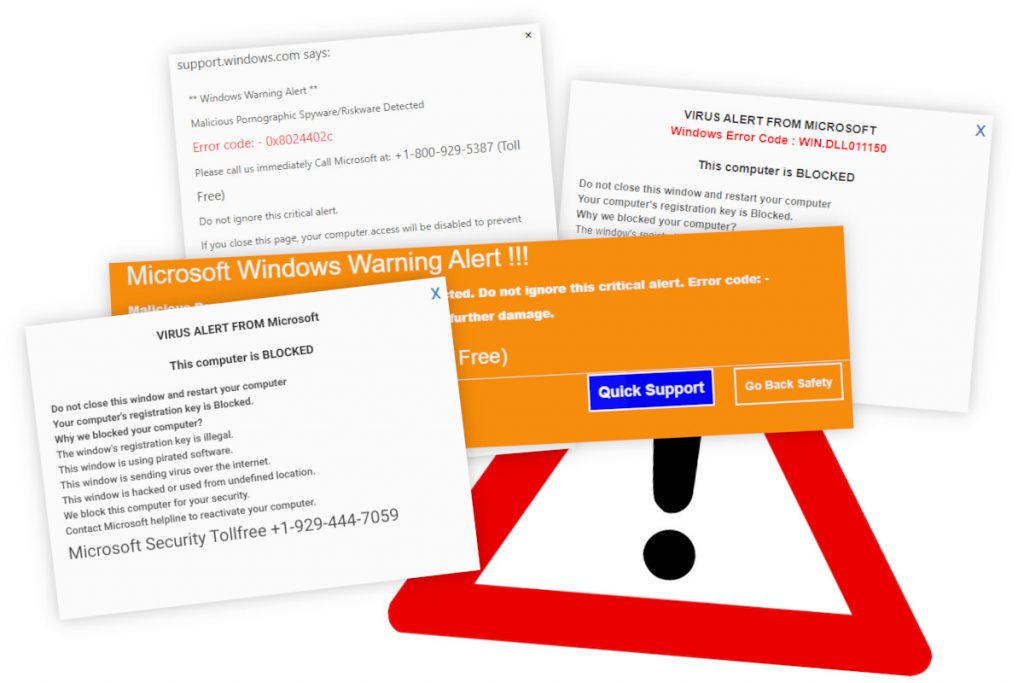
Today we’re revisiting the topic that we briefly discussed in email problems – spam. Spam emails are annoying, but they can also be dangerous. Malicious actors use email spam to steal our personal information and to spread malware. How can we recognize and avoid malicious spam?
Types of Malicious Spam Emails
Phishing
Phishing emails are scam emails that impersonate trusted companies (such as Microsoft and Apple). Usually, they seek to convince recipients that there’s a problem with their account. To solve this made-up problem, they link to a fake website, one that also impersonates the trusted company. This website asks the victim to provide their personal information. If they do, the data is sent to the scammers who were responsible for the phishing email.
One unfortunate example of dangerous spam is the many sketchy emails from “Apple”. Warnings that “your Apple ID is locked!“. Receipts of nonexistent iTunes and App Store purchases. Calls about iCloud accounts being hacked.
These fake messages are sent to Mac users with attachments and links to phishing websites – sites that ask them to reveal personal information. This information might include:
- Name
- Address
- Demographic information
- Credit card number and other payment information
- Usernames and passwords.
And people fill out those forms! And unwittingly send their very personal information to scammers. Because those phishing sites are very convincing. They copy the design of the site they’re impersonating and they use encryption (the padlock next to the address).
Malware
Other fake emails bring malware. Infected documents carry the Emotet trojan. Offers for free software hide ransomware inside them.
These emails could be about anything! An invoice, a document from your work, a shipping delay, a confirmation for an online purchase, a random link from an unknown person… The only condition is that there’s an attachment or a link to download the malicious file.
Ransomware commonly spreads via emails. It can cause terrible problems by destroying all user-created files on the infected computer.
Trojans also use email spam to infect PCs. They then turn those PCs into bots, install advertising malware, and steal passwords.

How to Stay Safe?
It’s important to be aware of the dangers that spam emails pose. So, how can you protect yourself?
Our old advice still applies. Don’t share your email address with just anyone. You can set up a special email account for use with untrustworthy sites. That way, you don’t have to reveal your personal and job emails when you don’t want to.
Using an email provider with a good spam filter is a great help. Staying vigilant is important. Trust your gut and don’t reveal your personal information when you aren’t comfortable doing so.
Use antivirus programs to scan your attachments and the sites you visit. But don’t solely rely on them, as malicious actors are always finding new ways to trick us.
If you have questions or worries, don’t hesitate to ask for help online. Even if it’s a small thing. Various community forums are always ready to offer advice. We’re also ready to help on any technical topic. Be careful and stay safe online.